četvrtak, 20. lipnja 2013.
srijeda, 19. lipnja 2013.
PhpMyAdmin version 3.5.7 vulnerable to Cross Site Scripting
phpMyAdmin is a free software tool written in PHP, intended to handle the administration of MySQL over the World Wide Web. phpMyAdmin supports a wide range of operations with MySQL. phpMyAdmin 3.5.0 to 3.5.7 versions are vulnerable to Reflected XSS in "tbl_gis_visualization.php", as mentioned in advisory. The reason for XSS is stated as insufficient sanitization of html output. Parameters vulnerable are "visualizationSettings[width]" and "visualizationSettings[height]" on "tbl_gis_visualization.php" .But there should be a valid session and valid database name for exploiting the vulnerability. Publically available exploitation details make javascript alert box to pop up, confirming the existence of Reflected XSS. The new updated version 3.5.8 is available on official website.
utorak, 18. lipnja 2013.
New sms spoofer across 100 countries
SMS spoofing is a relatively new technology which uses the short message service (SMS), available on most mobile phones and personal digital assistants, to set who the message appears to come from by replacing the originating mobile number (Sender ID) with alphanumeric text. Spoofing has both legitimate uses (setting the company name from which the message is being sent, setting your own mobile number, or a product name) and illegitimate uses (such as impersonating another person, company, product).
Simply visit and register here! Then start sending sms to any one with any number.
Sms spoofer: http://adf.ly/QkAfd
Simply visit and register here! Then start sending sms to any one with any number.
Sms spoofer: http://adf.ly/QkAfd
HOW TO CRACK WPA/WPA WITHOUT WORDLIST

Reaver implements a brute force attack against Wifi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA2 passphrases, as described in http://adf.ly/Q210f
Reaver has been designed to be a robust and practical attack against WPS, and has been tested against a wide variety of access points and WPS implementations.
On average Reaver will recover the target AP's plain text WPA/WPA2 passphrase in 4-10 hours, depending on the AP. In practice, it will generally take half this time to guess the correct WPS pin and recover the passphrase
VIDEO TUTORIAL: http://adf.ly/Qjzm2
VIDEO TUTORIAL: http://adf.ly/Qjzm2
TEXT TUTORIAL: http://adf.ly/Qk0N8
Hack remote computer via ip and open port
Literally, hacking is accessing something or somebody in internet without their permission or interest. While, speaking in summary, hacking is very easy job, it is like instead of using front door, finding the hidden door of a house and hijacking the precious things. Among all the hacking, hacking via IP address is one of the most common yet powerful beginning.
You may want to hack the website and put your advertisement there or grab some database information In this type of hacking, you are playing with the web server’s computer instead of the administrator’s computer. Because, www.website.com is hosted in separate web server rather than personal computer.
Another can be accessing your friend’s computer from your home. Again this is IP based and this is possible only when your friend’s computer is online. If it is off or not connected to internet then remote IP hacking is totally impossible.
Well, both of the hacking has the same process. Let’s summarize what we must do.
- Confirm the website or a computer you want to hack.
- Find or trace their IP address.
- Make sure that IP address is online
- Scan for open ports
- Check for venerable ports
- access through the port
- Brute-force username and password
Now let me describe in brief in merely basic steps that a child can understand it.
First, getting the IP address of victim.
To get the IP address of the victim website, ping for it in command prompt.
For example,
ping www.google.com
will fetch the IP address of Google.com
This is how we can get the IP address of the victims website.
How about your friend’s PC? You can’t do www.yourfirend’sname.com, can you? Finding your friend’s IP address is little tough job, and tougher it is if he has dynamic IP address that keeps changing.
One of the widely used method to detect IP address of your friend is by chatting with him.
You might find this article helpful
- How to get the IP address using MSN/Yahoo/Pidgin messenger
Now you got the IP address right? Is it online?
To know the online status just ping the IP address, if it is online it will reply.
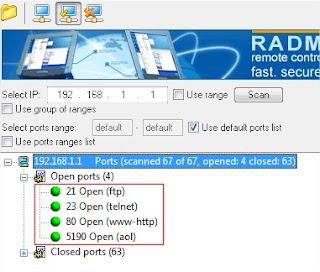
If the IP address is online, scan for the open ports. Open ports are like closed door without locks, you can go inside and outside easily.
Use Advanced Port Scanner to scan all open and venerable ports.
Now you’ve IP address and open port address of the victim, you can now use telnet to try to access them. Make sure that you’ve telnet enabled in your computer or install it from Control panel > Add remove programs > add windows components.
Now open command prompt and use telnet command to access to the IP address. Use following syntax for connection.
telnet [IP address] [Port]
You’ll be asked to input login information.
If you can guess the informations easily then it’s OK. Or you can use some brute-forcing tools like this one: Brutus, THC
- Hydra
In this way you’ll able to hack remove computer using only IP address